What is Two Factor Authentication (2FA/MFA)?
Important – The 2FA mechanism used by Foldr relies on an accurate system clock so it is vital that the system clock on the Foldr appliance is correct and remains in sync.
Introduction
It is recommended to use NTP as the Foldr server time source – more information is available here
Two factor authentication is a security feature that typically requires the user to provide a second factor when logging in. i.e. they must provide something they have, in conjunction with something they know before they are authenticated successfully. 2FA improves assurance of knowing that user A logged into a system, actually is user A, and not another person that may have simply obtained their network credentials.
In the use case with Foldr, something the user knows is their Active Directory username and password. Something they have is an ever changing time-based one-time password (TOTP / OTP) delivered via a third party application. The third party application in this case being an authenticator app installed on a smartphone or tablet.
The OTP based two factor authentication mechanism used in Foldr v4 has been adopted by many of the leading software vendors as a robust method of authenticating users; more information on the TOTP algorithm is available here.
This feature enables the administrator to require selected individuals or groups of users to comply with the 2FA requirement at login before they are granted access to resources via Foldr. 2FA can be made optional or enforced upon users depending on local security policy. If 2FA is optional a user can enable it within ‘Security Settings’ when logged into the Foldr web app. A user is always required to enter their username and password when enabling or disabling this feature.
To use the 2FA feature with Foldr, the recommended method of generating the user’s one time passwords is by using an authenticator app on a smartphone. There are numerous free apps that provide this facility for all major mobile platforms, however two that work well are Authy and Google Authenticator:

If a user does not own a compatible device to run an authenticator app, plugins are also available for desktop browsers (for example, Authy is available for Google Chrome)
Enabling 2FA for Users
The administrator can enable 2FA for specific users or groups within Foldr Settings >> Security > Multi Factor >> Users & Groups tab. There are two possible deployment methods – required (enforced) or optional (user can enabled 2FA through the web or mobile apps at a time of their choosing).
The example below shows enforcing 2FA for all members of the Active Directory security group ‘Marketing’

The next time a user of the Marketing groups signs into Foldr (or interacts with the Foldr interface if already signed in) they will be prompted to enrol.
If the Foldr admin uses the Optional setting instead of Required, a user can enable 2FA at a time of their choosing in the Foldr web app > Me menu.
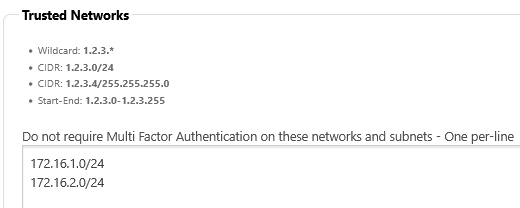
Trusted Networks
It is possible to specify specific networks/subnets or individual IP addresses that are considered Trusted. When trusted, clients connecting from these locations will not be required to pass 2FA/MFA to sign into Foldr. This is typically used to specify internal subnets in the organisation where MFA is not required as users signing in are to be considered trusted by default.
This setting is configured within Foldr Settings > Security > Mulit Factor > Settings > Trusted Networks
In the example below, clients signing in from networks 172.16.1.0 and 172.16.2.0 will not be prompted for 2FA codes when signing in to Foldr.
User Enrolment
The basic process of user enrolment is as follows:
- User installs their chosen authenticator app on smartphone or tablet
- User logs into Foldr using Active Directory credentials
- User scans the QR code of their shared secret using an authenticator app and optionally notes emergency backup code
- User verifies enrolment by entering 6 digit OTP shown in the authenticator app to complete login
- User is now enrolled in 2FA
When a user logs into Foldr and 2FA is mandatory, they will be prompted with the enrolment screen.

To enrol successfully, the user must create an account within their chosen authenticator app, and select SCAN QR CODE.
If the scan QR Code option is not available, you can manually enter the 28 alphanumeric secret shown below the QR code image.
Authy and Google Authenticator screenshots shown below after completing the enrolment process, note the six digit OTP code being shown in each app.

The user will now be prompted to enter their OTP each time they authenticate with Foldr.

NOTE – The one-time password changes every 60 seconds (30 second countdown per code within the authenticator app, plus a 30 second grace period). Due to the fact that the OTP relies upon the current time and the shared secret associated with the user, it is vital that the system clock on the Foldr appliance is correct and remains in sync.
It is recommended to use NTP as the Foldr server time source – more information is available here
Trusted Devices
By default, this admin setting is enabled, however the administrator can disabled or enabled this setting on a per app basis. A global trust setting is available also under Foldr Settings > Security > Multi Factor > Settings. Granular trust settings per app are available in the Foldr Settings > Security > Devices tab.
Once a user has successfully passed 2FA they can mark the device as a ‘trusted’ by using the toggle provided on the OTP code entry screen. Once their device app/browser is marked as trusted from this point on they will not be required to enter the 2FA OTP code when signing in. It should be noted that each browser is considered independently on the same computer. i.e. If a user marks trust this device in Google Chrome, they will still be forced to enter the OTP in Firefox

Managing Trusted 2FA devices/apps
A users trusted devices can be viewed within ME > Security Settings, when logged into the web app. These trusted devices/apps/browsers may be removed here if required

User devices may be deleted if required by the Foldr admin in Foldr Settings > Users & Groups > Devices. Deleting a device from this list will remove its trusted status for 2FA.

Granular Trusted Devices (client app type)
The administrator can configure granular trust settings on a per app basis and also whether each client app type may be trusted by group and location (network subnet) within Foldr Settings > Security > Multi Factor > Devices. The example below shows trust settings for the iOS app.

Trust settings may be configured individually for web, Windows Desktop, Windows Server, macOS, iOS and Android apps.
Backup Codes
Emergency backup codes are enabled by default but may be disabled by the administrator on the MFA configuration screen. The backup code is used by the user to reset the 2FA status of their account, which would be useful if they lose access to their authenticator app or the device running it is lost or stolen.
To use a backup code the user can select the link on the MFA code entry screen. Providing the correct code is entered, the user will then be prompted to re-enrol immediately if 2FA is required on the account.
Resetting a user’s 2FA status
Within Foldr Settings > Security > Multi Factor > Users an administrator can reset a user’s existing 2FA settings by clicking the inline X button next to the username.
![]()
When the reset button is clicked, the user is removed from the list and they will be forced to re-enrol at next login if they fall under the required/mandatory 2FA policy.
WebAuthn Support (signing in with physical security keys)
To complement 2FA/MFA, Foldr also supports signing in with physical security keys and biometrics using WebAuthn. More information about this feature can be found here.
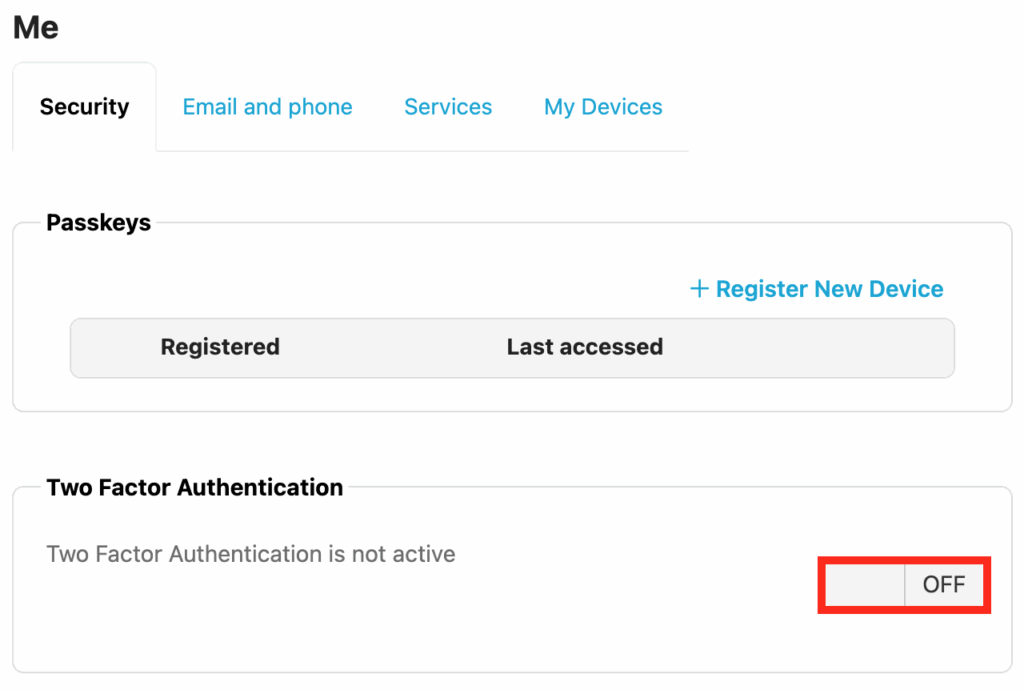
Enabling MFA for Foldr admin
When signed into Foldr Settings, the Foldr admin user can enable MFA (or passkeys) using the ME tab in the top-right menu.
This will load the ME tab in the Foldr (user) web app. Click the OFF toggle under Two Factor Authentication and proceed through the enrolment screen as described above.