The Foldr server can operate as a SAML single sign-on Identity Provider (IdP) or Service Provider (SP).
When acting as the Service Provider, the user is redirected to a third-party IdP such as Active Directory Federation Services, Microsoft Office 365/Azure, Google or Okta to sign in before being directed back to the Foldr app ready to access their files. If the user is already signed into their IdP (Okta in this case), Foldr web app users will sign in automatically.
Security Considerations
Service Accounts and User Passwords for SMB share access
Active Directory and traditional Windows file services have no concept of SAML or SSO access tokens. As such, when users are signing into the Foldr appliance without directly providing their password to the system, it is not possible for Foldr to provide the usual granular ACL / security permission access to the shares for that user. The administrator has two different options to this problem:
1. Use pre-defined service accounts in the Foldr Settings back-end and connect to each configured share with a master service account, ensuring they select ‘Use service account for all access’ on the share configuration screen. This approach does not allow Foldr to respect a users’ actual security permissions and will respect the permissions that apply to the service account user. The administrator can still control read or write access to each share for the service account using the share permissions in Foldr Settings >> Shares.
2. (Recommended) Prompt users for their password the first time they access the system by SSO. Once the Foldr appliance has the users password, it is encrypted and stored within the configuration database and can then be used for future sessions. A benefit of this approach is that service accounts are not required for access to SMB shares and Foldr can operate in the normal manner of respecting all existing security ACLs on the file servers providing access to the shares / data. You can enable the prompt for network credentials feature when enabling the SSO service within Foldr Settings >> Single Sign-On >> Service Provider.
Setup Process
1. Ensure Foldr is publicly accessible and that a signed SSL certificate is installed on the server. If you do not already have an SSL certificate, consider using the built in support for Let’s Encrypt to obtain one at no cost.
2. Sign into the Okta Admin portal using your administrative credentials and click Applications > Applications from the left hand panel
3. Click Create App Integration

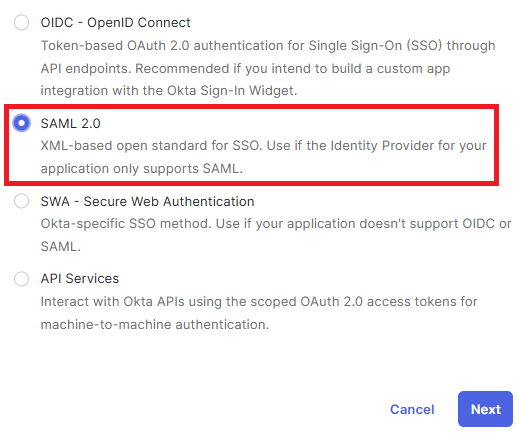
4. Select SAML 2.0 and click Next
5. Give the app a suitable name, optionally provide an icon and click Next
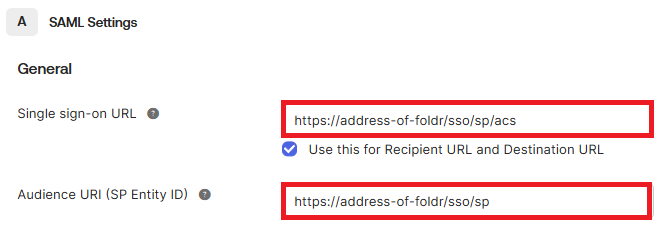
6. In the Configure SAML tab configure the Single sign-on URL and Audience URI fields as follow:
Single sign-on URL = https://address-of-foldr/sso/sp/acs
Audience URI = https://address-of-foldr/sso/sp/
Replacing address-of-foldr above with the external / public URI of the Foldr server
7. All other SAML settings on this tab can be left as default. Click Next
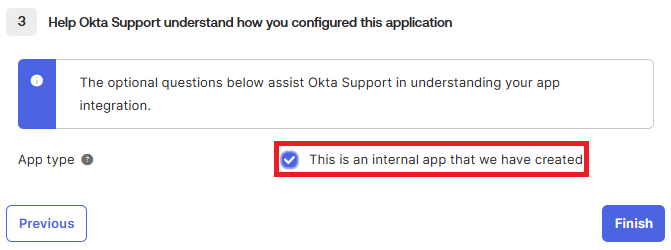
8. In the Feedback tab, either provide Okta with feeback for the Foldr integration and provide a link to this article in the field supplied (https://foldr.com/foldr-support/single-sign-on/foldr-as-a-service-provider-sp-with-okta-sso/) or alternatively, simply select This is an internal app that we have created and click Finish
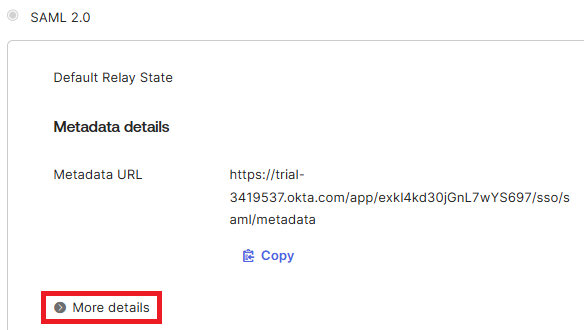
9. The SAML summary screen will be displayed. Click More details as highlighted.
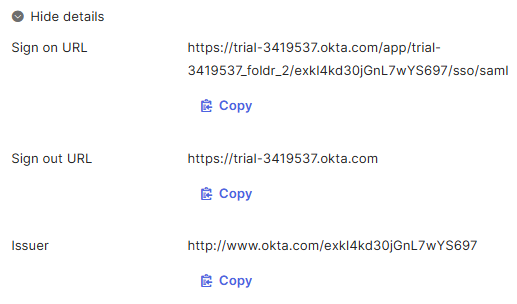
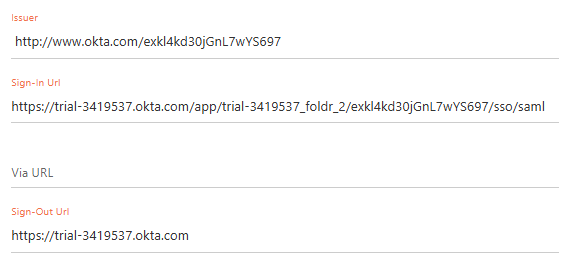
10. Copy the Sign on URL, Sign out URL and Issuer values
11. Download the Okta Signing Certificate

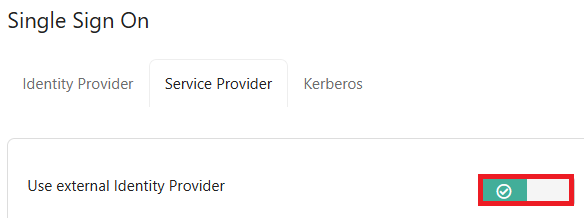
12. Navigate to Foldr Settings > Single Sign On > Service Provider and Enable the toggle Use external Identity Provider
13. Select the required user redirection settings from the available dropdown.
Redirect all LDAP users – Requires users to enter their Active Directory username first into the Foldr sign in UI, and then if the user is found in Active Directory, the user is redirected to Okta.
Redirect selected users & groups – Allows the administrator to select which Active Directory or local Foldr users & groups will be redirected to Okta
Redirect all users – The Foldr sign in page is not shown. All users are automatically redirected to Okta to sign in.
14. Paste in the Okta supplied Sign on URL, Sign out URL and Issuer values into the relevant fields in Foldr Settings
15. Open the Okta signing certificate, downloaded at step 11 in a text editor. Paste the certificate into the Validation Certificate box in Foldr Settings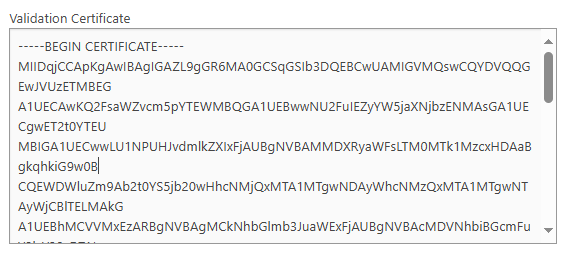
16. Click Save Changes
17. Navigate back to Okta, and select Applications > Applications and edit the Foldr app created for the SSO integration. Click Assignments
18. Click Assign > Assign to People or Assign to Group as required. In this example, we are assigning the Foldr app integration to the builtin ‘Everyone’ group. Search for and adjust as required for your environment.
19. After searching for the required user(s) or group click Assign
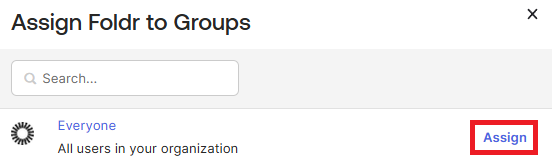
The summary panel will update to reflect your selection
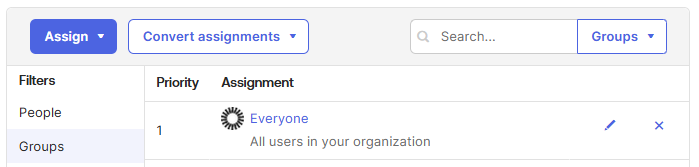
The SSO integration is now complete. A user attempting to sign into Foldr should be redirected to Okta’s sign-in page based on the user redirection settings selected at step 13.
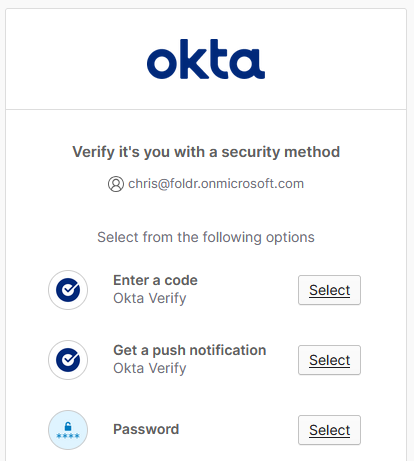
After signing into Okta and passing their MFA if enabled, the user should be automatically redirected to Foldr and presented with their storage locations in the interface.
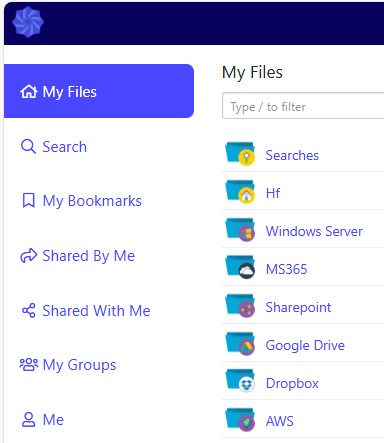
If the user is new / unknown to the Foldr server and if the toggle ‘Prompt LDAP users for network credentials’ was been enabled in the Foldr Settings > Single Sign On > Service Provider, the user will be prompted to provide their Active Directory password to access SMB shares.
App Compatibility
Okta SAML 2.0 Single Sign On is supported in all Foldr apps – web, mobile and desktop providing the ‘web sign-in’ feature is enabled on the server within Foldr Settings >> Devices & Clients. Note that web sign-in is ON by default for all app types.